
views
Instant messaging app Telegram's desktop app has been found to contain a major bug that leaked the public and private IP addresses of users, while initiating and during voice calls. This comes just days after Facebook revealed its largest ever data breach, with suggestions that as many as 90 million user accounts may have had their login tokens revealed to hackers because of an incorrectly configured software. Security researcher Dhiraj Mishra discovered that Telegram's desktop app was leaking both public and private IP addresses during voice calls due to its peer-to-peer framework. While smartphone users have the option of turning off P2P calls by changing the settings to other options by going to Settings > Privacy and security > Calls > Peer-To-Peer, there was no such option available for Telegram users on the desktop.
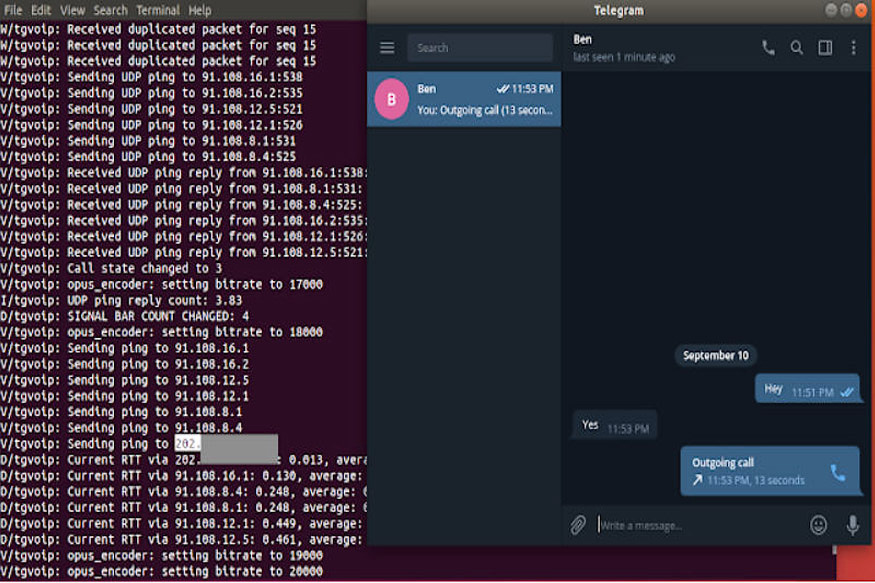
The company has fixed the issue in both the 1.3.17 beta and 1.4 versions of Telegram by giving you options to either disable peer-to-peer calling entirely or limit it to your contacts. The company’s security team has awarded the researcher EUR 2,000 (roughly Rs. 1,68,900) for reporting the bug in the app.
Recently, Telegram shot to fame globally because of its end-to-end encrypted servers and the resulting privacy for its user base. However, now the app is being blamed for harbouring illegal practices within the user base because of the same encryption. What's more, the authorities are unable to keep a check on these unlawful practices because of the encryption. As per a CNBC Aawaaz report, this is the prime reason why the app might be facing a complete ban in India soon.

















Comments
0 comment